
Welcome to our blog. In the Edgeless Systems blog, you can read about our products' latest features, use cases, insights into the confidential computing industry, experts' opinions, and much more.

Product

Insights

Insights

Insights
Security

Insights

Security
Insights

Security
Insights

Product

Insights
Security

Security
Insights

Product

Company
Insights

Insights
Security

Product

Product

Insights

Product
Tutorial

Insights
Fundamentals
Security

Insights
Fundamentals
Security

Insights

Tutorial

Product

Product

Insights

Security
Product

Product

Security
Insights

Security
Product

Security
Product

Security
Product

Product
Product

Insights

Insights

Insights

Product
Tutorial

Company

Insights

Product

Company

Company
Insights

Tutorial
Product

Insights
Security
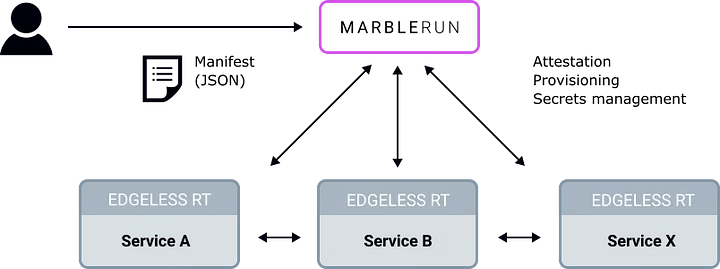
Product

Fundamentals
Insights
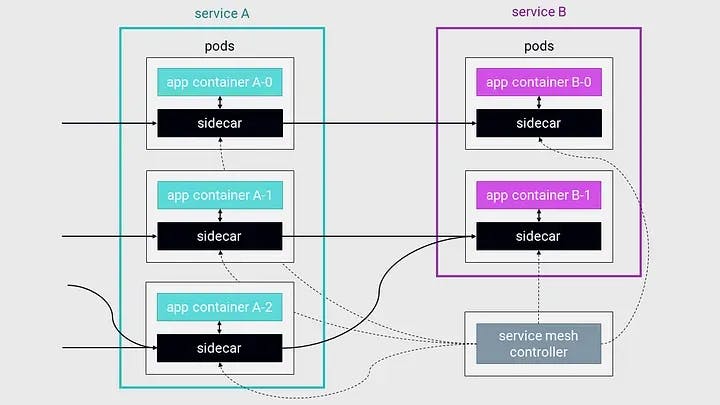
Fundamentals