
Blog
Software applications typically need to decrypt data to process it. This offers a big attack surface and poses security and privacy risks. Paired with increasing privacy concerns, this is often the reason for companies do not move to the cloud.
Homomorphic Encryption (HE) and Confidential Computing (CC) are both techniques to solve this issue by offering ways for complete data encryption at rest, transit, and in use. Therefore, they can pave the way to cloud transformation, enable new services, and address more customers. This is especially relevant for companies in highly regulated industries that need additional safeguards for the data they process.
This post looks at the differences between the two technologies and when to use which.
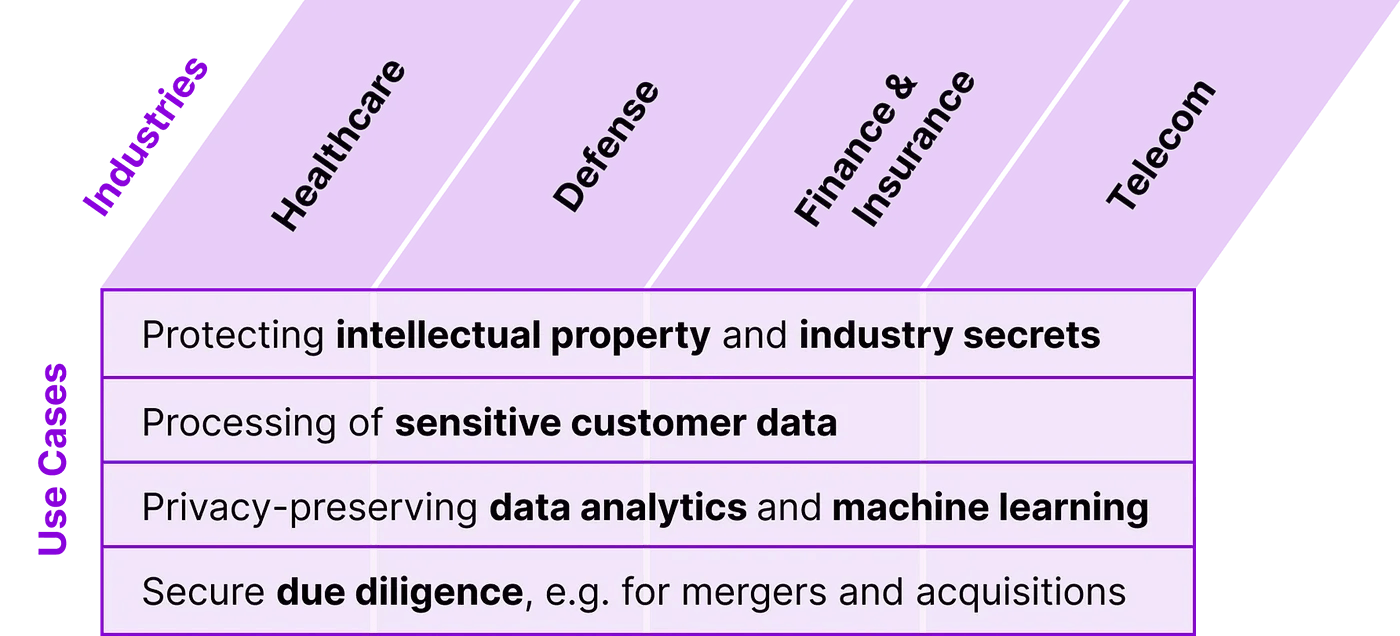
While almost every industry can benefit from Homomorphic Encryption and Confidential Computing in some way, there are certain cases where these technologies are needed the most. These include but are not limited to, storing and processing essential private and sensitive data (e.g. for predictive analysis) that may contain potentially privacy-compromising details.
Use cases and industries for which HE and CC are relevant:
Homomorphic Encryption is an extension of public-key cryptography with additional capacity for computing encrypted data without access to the secret key, meaning it does not need to decrypt data to process it. Homomorphic Encryption can perform computations on ciphertext (encrypted data). The result of these computations is identical to the result of the same operation on the plaintext without revealing any relationship between the ciphertext and the plaintext. Homomorphic encryption is software-based, meaning infrastructure providers can support it on most current hardware if needed.
The history of Homomorphic Encryption began in 1978. Today, we differentiate between three different levels of Homomorphic Encryption, that vary in the number of possible simultaneous encrypted operations.
- Partially Homomorphic Encryption supports only one operation, e.g., addition or multiplication.
- Somewhat Homomorphic Encryption supports two operations, but only certain operations.
- Fully Homomorphic Encryption supports any number of operations.
Because it is the strongest of the three, most research today happens in the field of Fully Homomorphic Encryption.
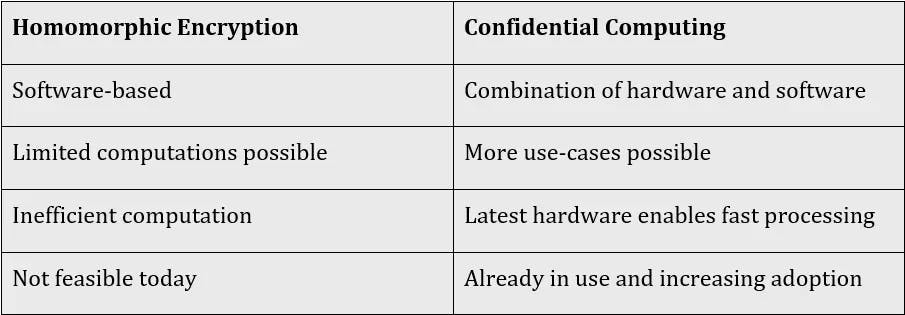
Since Homomorphic Encryption is software-based, it does not require specialized hardware. This makes it easy to adopt. The lack of specialized hardware for these compute-intensive tasks, however, is the main reason Homomorphic Encryption is still unpractically slow and has limited real-world use. Partially Homomorphic Encryption is usable now, but it only supports evaluating one function. The widely used RSA encryption algorithm could be considered an instance of PHE. In its textbook form, RSA allows for the direct multiplication of encrypted numbers, for example: RSA-encrypt (key, 3) * RSA-encrypt (key, 5) = RSA-encrypt (key, 15). Thus, one could build a simple privacy-preserving "number multiplication" service in the cloud just with the help of RSA.
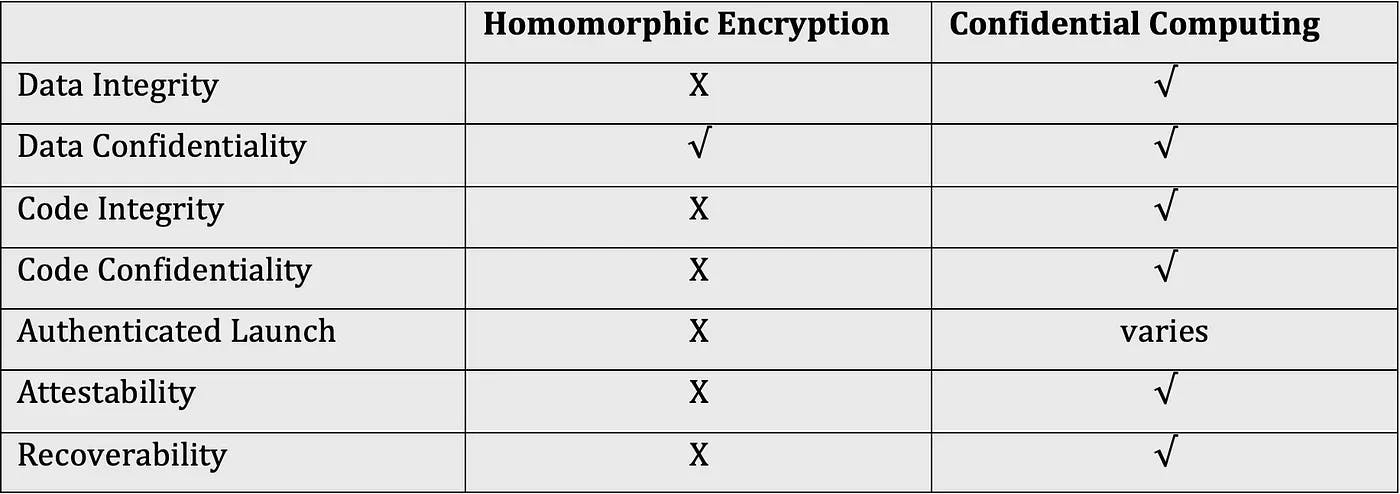
Fundamentally, all three forms of Homomorphic Encryption lack mechanisms for attestation, that would prove that precisely the desired operations were executed on the data. For example, in the above case of the number multiplication service, the user doesn't have any means to verify that the correct numbers were multiplied and how often. Instead of 3x5=15, a malicious or compromised service could for example return a valid encryption of 3x3=9. Thus, without attestation, there is still a lot of inherent trust needed, which many security-conscious users cannot afford in a public environment, such as third parties' clouds.
Confidential Computing protects data in use by isolating it from the outside world inside a CPU-enforced encrypted RAM region. This hardware-based Trusted Execution Environment (TEE) prevents unauthorized access to the data. This includes access from system administrators as well as other software and hardware components. Furthermore, TEEs provide an attestation mechanism, so users can always make sure their applications and data have not been tampered with.
CPU manufacturers and cloud providers have driven the development of Confidential Computing and created the Confidential Computing Consortium (CCC) with the Linux Foundation to oversee the adoption of Trusted Execution Environment technologies and standards.
The use cases for confidential computing are broader than FHE and include applications such as the collaboration between business partners while preserving intellectual property, and anonymous processing of data for training machine learning models.
Confidential Computing only works with certain hardware. This limits the places it can run, but developers can take advantage of specialized hardware which enables optimized performance. Today, all major public infrastructure providers such as Amazon, Google and Microsoft have adopted hardware that support Confidential Computing, like Intel SGX or AMD SEV-SNP, and continue to deploy new ones. There are development kits that offer emulation modes to test applications with standard processors before deploying code to real supported environments.
One of the biggest advantages of Confidential Computing over Homomorphic Encryption is the attestation mechanism which ensures data and code integrity.
Both Homomorphic Encryption and Confidential Computing offer great potential for protecting sensitive data in times when data is a valuable asset. They can enable cloud adoption and generate more value from privacy-critical data even in highly regulated industries.
The technical differences between how they protect data aside, the major difference between them is that Confidential Computing is already in active use, while Homomorphic Encryption is still in the experimentation phase and real-world applications are limited.
One approach is to adopt Confidential Computing now and explore Homomorphic Encryption as a possibility for the future.
Edgeless Systems can support and accelerate the adoption of Confidential Computing. With our product Constellation, it is possible to move entire Kubernetes clusters and workloads to a secure environment with a simple lift and shift. If you want to learn more about Confidential Computing, follow Edgeless Systems on LinkedIn and Twitter, and star our OSS projects on GitHub.