Blog
Are you interested in confidential computing but not sure where to start? We're here to help. Let's take a look at the basics of confidential computing, the types of problems that you can solve with it and some use cases that provide some insight into the game-changing nature of this field.
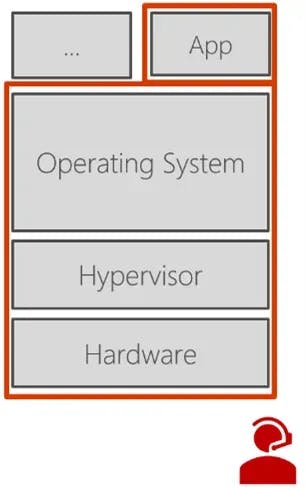
The fundamental problem can be summarized in one short sentence: computers are still not trustworthy enough. Customers do not trust companies with their data, companies do not trust the cloud, nobody trusts anyone. The underlying reason is that our compute stacks look like the one pictured --- we have apps, we deploy them on our operating systems, which run on hypervisors, which in turn run on hardware, which is installed and administered by people. If we are using conventional security technologies, we have to trust this entire stack. This leads to a significant attack surface, depicted in red. Basically, things can go wrong on any layer of this stack, including the people who run it.
Enter the solution: Confidential Computing.
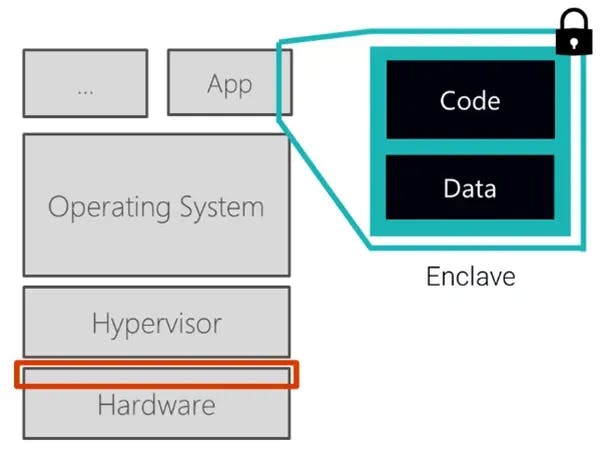
Confidential computing is all about processing data in secure enclaves, which is a breakthrough approach. In simple terms, an enclave is a trusted execution environment (TEE) provided by the hardware into which you can load your code. This allows you to run your data and code in isolation, enabling you to process data without having to fear access or manipulation from the outside. Doing this drastically reduces the attack surface, which therefore lowers the trust requirements to your own code and the hardware that creates the enclave.
Enclaves are available on many modern CPUs and can be created dynamically to make an untrusted system trustworthy. As a programmer, you can tell the CPU to create an enclave with normal CPU instructions and then load an arbitrary program into the secure enclave. Secure enclaves have four defining security properties, which are as follows:
These four defining features are available in various hardware implementations, of which Intel SGX might be the most well-known. Intel SGX was the first real implementation of secure enclaves in mainstream CPUs. A few years later, AMD SEV was introduced, and very recently Apple announced the M1 chip. Finally, there is also an implementation of RISC V, which according to our available sources has not been shipped in a commercial product yet.
There are also other less recent approaches such as ARM TrustZone, HSMs or TPMs --- these technologies typically have one or two of the defining features but not all of them. What we define as Confidential Computing requires all these four properties to be met.
Let's take a closer look at remote attestation, which might be the most important feature. Remote attestation works in several steps: First, if you are creating your enclave on an untrusted system, the CPU will measure or hash the initial contents of the enclave and the configuration of the arc length. This is a cryptographic cache and could for example be a sha 256 hash. Then, while running, the enclave can request a certificate from the CPU for parts of the data that is being produced. This certificate is also referred to as a "quote". Afterwards, the CPU produces a signature over the hash of the measurement and the data, binding the enclave contents, configuration and data produced. Each CPU has a unique private key that is burnt into it using fuses. Finally, a remote party such as a client, can verify this signature which proves that the data comes from a genuine SGX enclave.
If this sounds too technical, you can think of a secure enclave as an extremely secure black box that you can give your code and data to. This black box will crunch on that data using your code and provides you with results over a secure connection. To provide proof, you receive a certificate that precisely states that the results were produced using your code and your data, while no one else could access any of this.
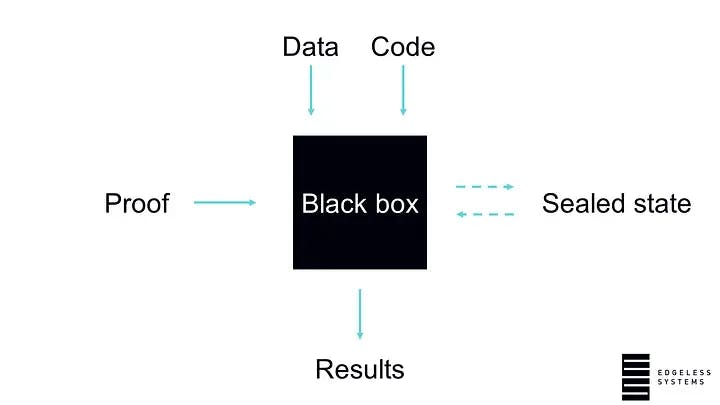
To sum it up, confidential computing enables encryption at runtime and adds verifiability of data processing.
Benefits and use cases of confidential computing
The first benefit that comes to mind is how confidential computing changes cloud security. Running workloads in secure enclaves enables entirely new security standards that prevent breaches, malware, malicious insiders and keep hackers out. By applying this to cloud infrastructures, this allows you to use the cloud almost like on-premises if you are running everything in secure enclaves --- because not even cloud providers can access your data or code, eliminating the trust requirement. In the next few years, this could become the primary use case for confidential computing and change how companies set up their IT infrastructure.
But that was only one single use case. If you think about the features we discussed previously, they open exciting new applications that have not been possible before. For example, you can analyse data without ever accessing it directly and prove via remote attestation that you did not look at it. This could change the way companies process customer data, preserving the privacy of their clients while doing so. Or you can create new business models --- the security properties of enclaves allow for sharing data without actually revealing it to another party. This allows for joint data processing while making sure that everyone can only access the results.
We hope this article was able to give you a broad overview of the necessity, inner workings and benefits of confidential computing --- Click here if you would like to see the current landscape of CC projects and how they fit together.
This blog post was delivered as a talk by Felix Schuster (CEO / Co-Founder, Edgeless Systems) at the Open Confidential Computing Conference 2021. You can watch the full recording on YouTube.